Abstract
Platforms and users alike face an attribution crisis—rampant content misattribution, accelerated by viral sharing and AI-generated media, erodes trust, damages creator livelihoods, and creates steep regulatory and reputational risks. Without an immutable, automated way to connect creators to content, decision making at every level of the digital media ecosystem is compromised. Consumers cannot distinguish authentic from stolen content, creators lose revenue to content thieves, and platforms face costly disputes with weak evidentiary standards.
Trust Engine solves this by enabling verifiable, tamper-evident attribution at upload, surfacing attributions platform-wide through integrated badges and modals, so every stakeholder—consumer, creator, business, or policymaker—can make informed decisions, resolve disputes, and preserve trust at scale. When users encounter content, they can instantly verify who registered it first, view competing claims chronologically, and access creator identity verification—transforming attribution from guesswork into evidence-based decision-making.
Trust Engine's Solana-based attribution layer creates immutable creator-to-content connections at upload and surfaces them platform-wide via a Trust badge + modal. Stakeholders can see who registered first, view competing registrations chronologically, and inspect optional registrant attestations (Proof of Humanity, social account verifications). This turns attribution from guesswork into evidence-based decisions, even when multiple parties claim the same media.
The system addresses attribution challenges across short-form video platforms, global messaging applications, news organizations, and user-generated content marketplaces. Privacy-preserving by design through client-side hashing, the protocol achieves registration costs under $0.001 per asset with sub-second confirmation times, enabling internet-scale deployment without compromising creator privacy or platform performance.
Global Disclaimer: Trust Engine is neutral infrastructure; it exposes facts and leaves judgments to platforms, courts, and consumers.
Introduction & Problem Statement
The attribution crisis is fundamentally a decision-quality problem. Misattribution—worsened by rapid re-uploads and AI-aided edits—forces consumers, creators, and platforms to decide with incomplete evidence, eroding trust and misallocating value.
The core problem is uninformed decision-making at internet scale. Every day, billions of users, creators, platforms, and businesses make critical decisions about digital content without verifiable attribution data. This information asymmetry creates systematic failures: consumers share content without knowing its true origin, creators lose revenue to unverifiable theft claims, platforms moderate disputes with weak evidence, and businesses face legal exposure from unverifiable ownership assertions.
The Cost of Uninformed Decision-Making
When attribution cannot be verified, every stakeholder operates with incomplete information, leading to suboptimal decisions that compound into systemic trust breakdown and economic losses.
Sector Example: Short-Form Video Platforms
- • Decision Problem: Platforms cannot determine which creator deserves algorithmic promotion when multiple accounts claim the same viral content
- • Financial Impact: Original creators lose $4,000-$100,000+ per viral theft as revenue flows to unverifiable claimants[R1]
- • Platform Consequence: 129.3M videos removed quarterly due to attribution disputes, requiring expensive manual review[R2]
- • Trust Erosion: Creator strikes and policy changes costing platforms millions when attribution systems fail[R3]
Sector Example: Global Messaging Platforms with Commerce
- • Decision Problem: Businesses cannot prove ownership of marketing content when competitors steal and repost
- • Financial Impact: Customer acquisition diverted to content thieves in $400B+ transaction ecosystems[R4]
- • Platform Consequence: Costly dispute resolution without immutable evidence standards
- • Trust Erosion: Brand confusion and competitive disadvantage from unverifiable claims
Sector Example: Multinational News Organizations
- • Decision Problem: Courts and competitors cannot verify temporal precedence of breaking news content
- • Financial Impact: Millions in legal costs defending attribution rights and lost syndication revenue[R5]
- • Platform Consequence: Expensive manual authentication processes for legal proceedings
- • Trust Erosion: Journalistic credibility undermined by attribution disputes
Why Current Solutions Cannot Enable Informed Decisions
Platform-Specific Tools: Cannot provide cross-platform verification or legal-grade evidence for informed decisions[R3]
Content Authenticity Standards: Address "how was this made?" not "who created this?" limiting decision-making context[R6]
Copyright Systems: Multi-week resolution times prevent real-time informed decisions for viral content
Manual Verification: Does not scale to billions of daily content decisions across global platforms
The Solution Requirement: Enable informed decision-making at internet scale by providing verifiable, immutable attribution data that stakeholders can reference instantly. This transforms attribution from subjective judgment into objective evidence evaluation, supporting better decisions for consumers, creators, platforms, and legal systems.
Regulatory frameworks including the EU Digital Services Act[R7] and emerging AI safety guidelines[R8] increasingly require platforms to make content decisions based on verifiable evidence rather than subjective assessment. Trust Engine provides the missing infrastructure layer that enables evidence-based attribution decisions at the scale and speed required by global digital media platforms.
System Overview
Trust Engine enables informed decision-making by providing verifiable, tamper-evident attribution for every piece of digital content. When users encounter media—whether sharing, moderating, purchasing, or adjudicating—they can instantly access immutable evidence about who created it, when it was registered, and what competing claims exist. This transforms attribution decisions from guesswork based on reputation or platform-specific signals into evidence-based evaluation using cryptographic proof and transparent chronology.
Trust Engine's Solana-based digital media attribution infrastructure creates immutable creator-to-content connections at upload. This enables digital media consumers and platforms to make informed decisions by referencing a public, tamper-evident registry—surfaced via platform-integrated badges and modals that show chronological registrations, surface registrant attestations and registration facts, and support cross-platform content authenticity, even when media is modified.
Core Data Flow
Content creation or upload
SHA-256 fingerprint generation
Immutable blockchain anchor
Evidence Bundle retrieval
Downstream attribution logic
Privacy Guarantee: Original content never transmitted; only cryptographic fingerprints and minimal metadata stored on-chain.
Without Attribution Infrastructure
- • Disputes rely on manual search and subjective signals
- • No universally verifiable temporal precedence
- • Platform-specific silos; weak portability
- • Evidence assembly is ad-hoc and slow
- • Identity context inconsistent across products
With Trust Engine
- • Programmatic precedence lookup (on-chain timestamps)
- • Immutable, portable registrations across platforms
- • Structured evidence bundles for policy/legal review
- • Optional registrant attestations (PoH, social)
- • Consumer-facing badge + modal for informed decisions
Temporal Precedence Module
Anchors "who registered what, when" on-chain; exposes sortable, verifiable chronology. Provides cryptographic proof of registration order for dispute resolution.
Identity Attestation Module
Optional wallet-bound attestations (Proof of Humanity; social handle proofs). Supports key rotation: creators can rotate wallets and post a new attestation; older attestations can be marked revoked via a public revocation list (registration records remain immutable).
Competing Claims Module
Displays all registrations that share the same content hash, ordered by time. No ownership arbitration; pure facts.
Similarity Linking (Community-Voted)
Lets users report and vote that two different hashes are visually similar (e.g., screen-record, crop, watermark removal). These are advisory links surfaced in a dedicated Similar Versions tab to help discover the likely original despite transformed fingerprints. No machine learning; it's community-curated visibility.
Note: Similarity voting is a planned feature for future implementation.
Clarification: Trust Engine does not arbitrate legal ownership or truthfulness of narrative claims; it exposes verifiable facts (timestamps, wallet bindings, and user-provided attestations).
Market Definition
Platforms with 100M+ users where content attribution failures create massive financial, legal, and regulatory consequences.
Note: Brand names are illustrative and non-affiliative; no partnership is implied.
Archetype A: Short-Form Video Platform (e.g., TikTok) — illustrative ($33.1B Revenue, 1B+ Users)
Attribution Crisis:
Black Creator Strike forced platform-wide policy changes costing millions. 129.3M videos removed quarterly due to attribution disputes. Creators lose $400-$1,000 per million stolen views under Creator Rewards Program.
Trust Engine Value:
Immutable temporal precedence eliminates 'who posted first' disputes. Community attribution discovery solves modified content theft. Creator retention through protected revenue streams.
Archetype B: Super-App with Commerce (e.g., WeChat) — illustrative ($16.4B Revenue, 1.38B Users)
Business Content Theft:
Mini-Program ecosystem generates $400B+ transactions annually. Content theft diverts customer acquisition and brand recognition, costing businesses thousands per incident.
Trust Engine Value:
Blockchain-verified business content ownership. Automated dispute resolution for Mini-Program operators. Cross-platform attribution for brand protection.
Archetype C: Global News Network — illustrative & MAJOR NEWS NETWORKS
Legal Attribution Costs:
Breaking news photo theft requires expensive legal enforcement. Lost syndication revenue when competitors steal exclusive content. Court cases requiring blockchain evidence authentication.
Trust Engine Value:
Legal-grade blockchain evidence for court proceedings. Immutable timestamps prove content precedence. Revenue recovery through protected syndication rights.
Platform Selection Criteria
Quantitative Requirements:
- • 100M+ monthly active users minimum
- • Billions in annual revenue at stake
- • Documented attribution crises costing creators/platforms significant money
- • Regulatory/legal pressure requiring attribution solutions
Decision Makers:
- • Platform executives and product leaders
- • Legal and policy teams managing creator disputes
- • Trust & Safety teams handling content moderation
- • Business development teams seeking competitive advantages
Solution Overview (Non‑Technical)
Trust Engine is a Solana-backed attribution layer that binds a creator's wallet to a content fingerprint at upload and surfaces that fact everywhere the content travels. A lightweight Trust badge opens a modal showing (1) the earliest registration and full chronology of exact-hash registrations, (2) a community-voted Similar Versions list for transformed copies with different hashes, and (3) optional Proof-of-Humanity and social verifications for registrants. Platforms and consumers use these signals to make independent, informed decisions—to credit, recommend, flag, or litigate—without Trust Engine ever deciding for them.
Trust Engine System Flow
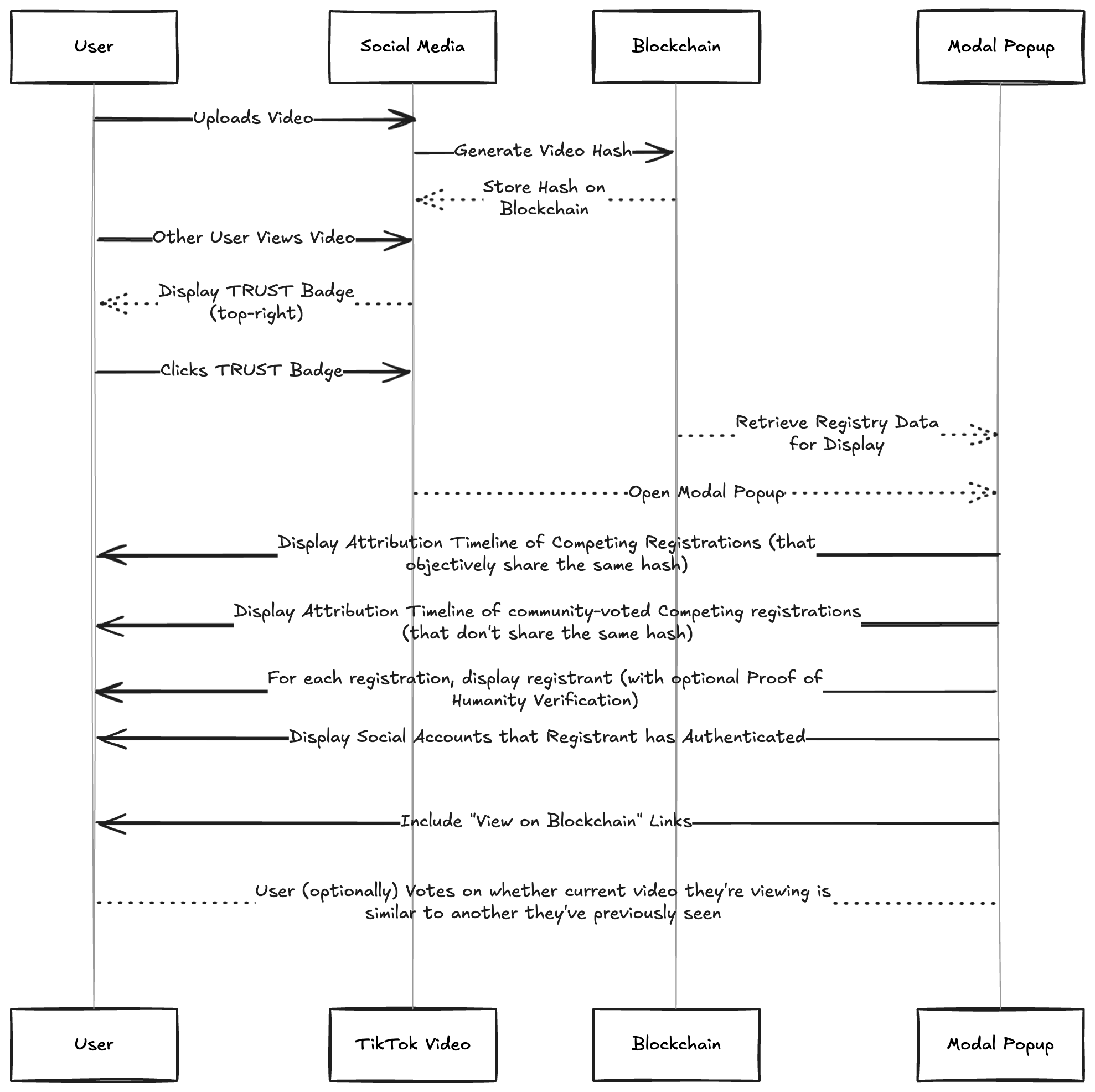
Figure 1: Complete Trust Engine workflow showing user upload, hash generation, blockchain registration, TRUST badge display, and modal popup with attribution timeline including competing registrations and community similarity voting.
Sequence alignment: Upload → Hash → On-chain store → Badge visible → Click → Modal fetch registry → Show Exact Matches (same hash) and Similar Versions (crowd-voted different hashes) → Optional user vote.
Objective "Who Posted First" Answers
Platforms can instantly determine which creator deserves algorithmic promotion, brand partnerships, or legal protection based on immutable registration timestamps, not subjective assessment.
Cross-Platform Content Authenticity
Users can verify content authenticity across platforms even when media is modified, enabling informed sharing and attribution decisions in multi-platform creator ecosystems.
Verified Creator Identity Context
Decision-makers can evaluate attribution claims with verified creator identity data, social proof, and reputation history, reducing reliance on platform-specific signals.
Transparent Competing Claims
All stakeholders see the same chronological attribution data and competing registrations, eliminating information asymmetries that enable content theft and false claims.
Automated Dispute Resolution
Platforms can automate attribution decisions using verifiable evidence rather than manual review, reducing costs while improving accuracy and consistency.
Legal-Grade Evidence for Courts
Legal proceedings can reference immutable blockchain evidence for attribution disputes, enabling faster resolution and stronger enforcement of creator rights.
Real-World Use Cases
Trust Engine transforms platform attribution crises into competitive advantages through immutable infrastructure. Each use case demonstrates real financial impact: how billions in creator revenue, platform liability, and business value get protected through verifiable attribution that enables informed decision-making at internet scale.
Use Case 1 — TikTok Viral Dance Attribution Recovery
Exploring 1 of 6 detailed scenarios
Context & Decision-Maker
TikTok Platform & Creator Community encounters a digital media authenticity challenge.
The Situation
Keara Wilson creates 'Savage' dance (300 followers), registers via Trust Engine during upload. Content goes viral with 50M+ views, 100+ accounts repost/remix without credit. Under Creator Rewards Program, original creator loses $20,000-$50,000 in monetization to content thieves.
Critical Decision Point
Which creator deserves algorithmic promotion and brand partnership opportunities?
Available Evidence
Trust Engine provides these verifiable signals:
Resolution & Value
Original creator retains $20K-$50K monetization, algorithm prioritizes authentic content, platform reduces 129.3M quarterly video removals through automated attribution resolution.
Market Size & Opportunity
Total Addressable Market: $15-25 Billion by 2027[17]
Attribution infrastructure represents a massive, underserved market within the $466.56B social media ecosystem.
Bottom-Up Market Calculation
Conservative Model (Platform Licensing + Usage Fees)
Growth Model (Revenue Share Approach)
TAM: $15-25B by 2027
- • Social Media Attribution Infrastructure: $5-8B
- • Enterprise Media Networks: $29.33B by 2029[18]
- • News/Media Attribution Recovery: $3-5B
- • Cross-platform creator tools: $2-4B
SAM: $3-5B
- • TikTok: $33.1B revenue, 1B+ users[19]
- • WeChat: $16.4B revenue, 1.38B users[2]
- • Major News Networks: $5-10B combined
- • 100M+ user platforms only
SOM: $375M-$1.5B
- • Conservative: Platform licensing model
- • Growth: 2-5% revenue share model
- • Year 3 achievable projections
- • Network effects acceleration
Market Validation: Proven Platform Demand
Platform Investment Evidence
- • TikTok's 2022 crediting tools: $10M+ investment[10]
- • Fox/Polygon Verify partnership: $5M+ commitment[13]
- • Adobe C2PA adoption: Industry standard recognition[11]
- • 39% attribution model failures create infrastructure gap[20]
Revenue Multiplier Effects
- • Creator retention value: 10x platform investment
- • Advertising premium: 15-25% higher rates
- • Regulatory compliance: Avoid 6% turnover fines
- • Network effects: Winner-take-most dynamics
Regulatory & Market Drivers: Why Now
Regulatory & Market Convergence: $15B+ Infrastructure Opportunity
EU Digital Services Act requires content accountability for platforms with 45M+ users. US Congressional hearings demand creator compensation solutions. NIST AI Safety Institute explicitly calls for attribution infrastructure[21]. Regulatory pressure, creator economy maturation, and AI content explosion create unprecedented demand for attribution infrastructure.
REGULATORY PRESSURE INTENSIFYING
EU Digital Services Act:
Platforms with 45M+ EU users must implement content accountability measures. Attribution infrastructure becomes compliance requirement, not optional feature.
US Congressional Hearings:
Creator compensation and platform responsibility under intense scrutiny. NIST AI Safety Institute explicitly calls for attribution infrastructure as public-interest tooling.
CREATOR ECONOMY MATURATION
Professional Creator Demands:
$1.3B+ monthly creator economy requires attribution infrastructure for revenue protection. Brand partnerships demand verifiable content ownership history.
Cross-Platform Strategies:
Creators building audiences across multiple platforms need portable attribution solutions. Platform lock-in becomes competitive disadvantage.
AI CONTENT EXPLOSION
Authenticity Confusion:
Deepfake technology makes content authenticity critical for platform trust. Synthetic media flooding platforms creates attribution infrastructure demand.
Platform Liability:
Hosting unattributed synthetic content increases legal exposure. Creator protection becomes competitive differentiator between platforms.
Market Timing Validation
Proven Platform Demand:
- • TikTok's 2022 crediting tools prove problem recognition
- • Fox/Polygon Verify partnership shows enterprise investment
- • 39% of attribution models failing due to privacy changes
- • Adobe C2PA adoption demonstrates market readiness
Infrastructure Gap:
- • Existing solutions focus on AI detection, not creator disputes
- • Platform native tools lack immutability and portability
- • No universal attribution infrastructure exists
- • First-mover advantage available in $15-25B market
Threat Landscape & Public‑Interest Urgency
Manipulated Media: National‑Security‑Scale Risk
US agencies (NSA, FBI, CISA) warn deepfakes threaten NSS/DoD/DIB; they publish mitigation guidance.
Wartime Psy‑Ops
2022 Zelensky surrender deepfake; better forgeries could be worse
Financial Markets
Fake Pentagon explosion image briefly moved US equities—real financial impact
Elections
AI robocalls impersonated sitting president; charges and penalties followed
Courts
Rising "deepfake defense"; rules and standards being revisited
Financial Crime
FinCEN warns GenAI used to subvert KYC and commit fraud
Law Enforcement
AI‑generated CSAM burden escalating
NIST AI Safety Institute
Explicitly calls for provenance infrastructure as public‑interest tooling.
System Architecture (High‑Level)
Platform Integration Flow
Upload → Hash → Register → Badge Display → User Decision: A minimal integration surface enables platforms to create immutable creator-to-content connections at upload, display attribution badges on content, and provide users with chronological attribution data for informed decision-making.
Creator uploads content
SHA-256 fingerprint
Immutable timestamp
TRUST widget shown
Informed attribution
Platform Benefits: Automated dispute resolution • Reduced moderation burden • Legal protection • Creator retention
System Architecture (Low‑Level)
1) Client‑Side Hashing (Privacy‑Preserving)
Files are hashed locally in the browser/client to generate a unique SHA-256 fingerprint. The original file never leaves the user's device during this process, ensuring privacy-by-design.
// Web Crypto API example - runs entirely in browser
async function hashFile(file) {
const buf = await file.arrayBuffer();
const hash = await crypto.subtle.digest('SHA-256', buf);
return Array.from(new Uint8Array(hash))
.map(b => b.toString(16).padStart(2, '0'))
.join('');
}Privacy Guarantee: The hash uniquely identifies the content but cannot be reversed to recover the original file. This enables verification without exposure.
2) IPFS Metadata Storage (Optional but Recommended)
Rich metadata is stored on IPFS for decentralized, content-addressed retrieval. Only metadata is stored, never the actual media content.
IPFS Data Structure:
{
"file_metadata": {
"contentTitle": "Human-readable content title",
"fileName": "original-filename.jpg",
"fileSize": 1234567,
"mimeType": "image/jpeg"
},
"public_metadata": "Optional description, tags, or context",
"content_hash": "a1b2c3d4...",
"identity_verification": {
"verified_name": "John Doe",
"verified_nationality": "US",
"provider": "self",
"nullifier": "user_id_hash",
"verified_at": "2024-01-15T14:30:25.000Z"
}
}Required Fields
- •
file_metadataobject - •
contentTitle,fileName - •
fileSize,mimeType
Optional Fields
- •
public_metadata(user descriptions) - • Custom metadata fields
- • Tags and categories
https://trustengine-ipfs.quicknode-ipfs.com/ipfs/{CID}3) Blockchain Registration (Solana)
The on-chain ContentRegistration account stores minimal, immutable data. Each registration costs ~200 bytes of blockchain storage.
pub struct ContentRegistration {
pub content_hash: [u8; 32], // SHA-256 hash of the media file
pub creator: Pubkey, // Registrant's wallet address
pub ipfs_cid: String, // Pointer to IPFS metadata (optional)
pub timestamp: i64, // Unix timestamp of registration
}Field Explanations:
- • content_hash: SHA-256 fingerprint uniquely identifying the media (32 bytes)
- • creator: Solana wallet public key that submitted the registration
- • ipfs_cid: Content identifier for IPFS metadata storage
- • timestamp: Unix timestamp when registration was anchored on-chain
4) Registration Data Flow
SHA-256 of media
Hash of metadata
Metadata → CID
Immutable record
Combined display
Data Separation Benefits
- • On-chain: Immutable proofs, tamper-evident timestamps
- • IPFS: Rich metadata, decentralized but updatable context
- • Privacy: Original files never stored anywhere
Required vs Optional
- • Required: content_hash, claim_hash, creator, timestamp
- • Optional: ipfs_cid (can be empty for minimal registrations)
- • Never stored: Private keys, raw media content
5) Wallet Types & Transaction Flows
Managed Wallets (Crossmint)
Crossmint Smart Wallet integration with server fee-payer sponsoring SOL transaction costs. API handles wallet creation and transaction signing.
Self-Custody Wallets
Action-link flow generates unsigned transaction for Phantom/Solflare wallet signing. Optional returnActionLink parameter creates 24-hour expiring action links.
6) Storage & Privacy Summary
Stored On-Chain
- • Content hash (32 bytes)
- • Creator wallet (32 bytes)
- • IPFS CID (variable string)
- • Timestamp (8 bytes)
- • Total: ~200 bytes per registration
Stored in IPFS
- • File metadata (name, size, type)
- • Content title/description
- • Public metadata/tags
- • Identity verification data (if present)
- • Content hash reference
Never Stored
- • Raw media content
- • Private keys
- • Sensitive file paths
- • Hidden metadata/EXIF
Registry, Discovery, and Identity Integration
What the Registry Serves
- • Binary, privacy‑preserving linkage: fingerprint → registrant with timestamps
- • Public verifiability & immutability: Anyone can verify a hash was registered at time T by account A
- • Identity layering: Users can connect social accounts and complete Proof of Humanity via self.xyz
- • Creator control: We do not dictate disclosures; no ownership arbitration and no disclosure arbitration
Back‑dated Creations
Authors can anchor fingerprints of prior works now. This doesn't rewrite history; it creates a tamper‑evident claim from this point forward.
Judgment Targets
Editorial, policy, legal, attribution, and investment decisions—hence neutral data, not verdicts.
Verification & TRUST Stamps
Search Methods
By File Upload
Local hash generation
By Hash String
Direct SHA‑256 lookup
By Creator Address
Wallet‑based search
Multi‑Claim Surfacing
We enumerate competing claims for the same fingerprint and order them chronologically.
TRUST Stamp Widget
A single‑tag script that can auto‑scan media elements, query the registry, and overlay a verification stamp:
<script
src="[PARTNER_WIDGET_URL]"
data-api-base-url="https://core-api-server.onrender.com"
data-stamp-position="top-right"
data-stamp-size="medium"
data-auto-scan="true">
</script>Verification Response (Illustrative)
{
"searchMode": "content_hash_and_wallet",
"totalResults": 2,
"registrations": [{
"contentHash": "a1b2c3d4...",
"registeredBy": "9WzDXwBbmkg8ZTbNMqUxvQRAyrZzDsGYdLVL9zYtAWWM",
"timestamp": "2024-01-15T14:30:25.000Z",
"registrationStatus": "Registered",
"attestations": { "proofOfHumanity": true, "social": ["x:@handle"] },
"explorerUrl": "https://explorer.solana.com/tx/..."
}]
}
}Utility Examples
News Photo Checks
Editorial verification
E‑commerce Assets
Product authenticity
NFT Platforms
Provenance display
Academic Materials
Research verification
Privacy Model & the "Hash Abstraction" Debate
Where Privacy Actually Matters
1. Bulk Protection Against AI Training
Registry can't be mass‑scraped for training data absent creator consent; badges don't yield systematic harvesting.
2. Legal/Regulatory Compliance
Privacy‑by‑design helps with GDPR/CCPA and emerging AI rules; essential for enterprise and international adoption.
3. Registry‑First Discovery Protection
Browsing hashes doesn't reveal files; protects early registrations, sensitive content, and competitive workflows.
If Privacy Were Removed
Simpler architecture, clearer UX, easier developer integration
BUT: Compromised registry‑first privacy
If Privacy Is Maintained
Stronger positioning, systematic protection at scale, compliance‑friendliness, and creator trust.
Platform Integration & API
Platform Integration Value
Platform Benefits:
- • 60-80% reduction in dispute resolution time
- • $5M+ annual savings in moderation costs (TikTok scale)
- • Legal protection through blockchain evidence
- • Creator retention through attribution protection
- • Competitive differentiation in creator economy
Integration Components
Upload API
Hash Generation
Badge Widget
Registry Query
Dashboard
Platform Integration Examples
Content Registration
POST /register
{
"contentTitle": "My Video Title",
"walletAddress": "9WzDXwBbm...",
"walletType": "managed", // or "self"
"contentHash": "a1b2c3d4...",
"fileMetadata": { /* file info */ },
"metadata": "Optional description",
"returnActionLink": false
}Registry Search
POST /search
{
"contentHash": "a1b2c3d4...",
"walletAddress": "9WzDXwBbm..." // optional
}
// Returns chronological registrations
// and IPFS metadataDX Patterns
SPA
SDK + wallet connect
Server Apps
REST
Static Sites
Widget
Mobile
Native hashing + HTTP
CLI Example
trust-engine-cli register \ --file example.txt \ --contentTitle "My Document" \ --walletType managed
Architecture Flow
Competitive Landscape & Differentiation
Market Gap Analysis
Current solutions address adjacent problems but miss the core attribution crisis affecting billion-user platforms. Trust Engine fills the critical infrastructure gap.
AI Detection Tools (C2PA)[11]
What They Solve: Identify synthetic content and AI-generated media
Market Focus: Enterprise creative tools and content authenticity
Gap: Don't solve human creator disputes or temporal precedence
Missing: Cross-platform attribution for social media scale
News Verification (Fox/Polygon)[13]
What They Solve: Publisher content verification for news organizations
Market Focus: Enterprise news networks and media companies
Gap: News-focused, not social media creator economy
Missing: Creator identity verification and community-driven attribution
Platform Native Tools[10]
What They Solve: Basic in-platform crediting and attribution
Market Focus: Platform-specific creator tools
Gap: No immutability, blockchain backing, or legal-grade evidence
Missing: Cross-platform portability and automated dispute resolution
Copyright Systems
What They Solve: Legal copyright enforcement and DMCA processes
Market Focus: Legal protection for intellectual property
Gap: Take weeks while content thieves bypass detection in minutes
Missing: Automated attribution verification for platform scale
The Infrastructure Gap
No immutable infrastructure exists for billion-user platforms to resolve creator attribution disputes automatically while enabling cross-platform portability.
Market Need:
- • Immutable temporal precedence for creator disputes
- • Cross-platform attribution portability
- • Legal-grade blockchain evidence for court proceedings
- • Automated dispute resolution at billion-user scale
Trust Engine's Position:
- • Built the missing attribution infrastructure layer
- • Transforms platform policy problems into automated advantages
- • First-mover in $15-25B market opportunity
- • Network effects create massive competitive moats
Critiques & Our Response (Infrastructure vs. Arbitration)
False Premise
"Your data could lead users to wrong decisions."
Rebuttal
We're infrastructure. Like DNS or WHOIS, we publish neutral facts. Without Trust Engine, decisions are less informed, driven by unverifiable signals and subjective policy. With Trust Engine, decisions cite immutable timestamps, identity proofs, and transparent multi‑claim chronology.
Publisher Scenario
With TE: Same likely decision (credit the Reuters photographer), but now justified by precedence and verified identity rather than pure reputation.
Platform Policy Scenario
With TE: Honor/reject a takedown by referencing temporal precedence and identity proofs; outcomes become consistent and defensible.
Bottom Line
Imperfect information > no information. We increase transparency and reduce arbitrariness without removing user agency.
References
Additional Resources
Trust Engine Documentation: trustengine.org/docs
Platform Integration Guide: trustengine.org/platform
Technical Architecture: trustengine.org/whitepaper
Contact for Platform Partnerships: partnerships@trustengine.org
Appendices
Appendix A: Data Structures
A.1 Content Registration Schema
{
"content_hash": "string", // SHA-256 hash (64 hex chars)
"claim_hash": "string", // Hash of registration metadata
"creator": "string", // Solana public key (44 chars base58)
"ipfs_cid": "string", // Optional IPFS content ID
"timestamp": "number", // Unix timestamp (seconds)
"block_height": "number", // Solana block height
"signature": "string" // Transaction signature
}A.2 Identity Attestation Schema
{
"wallet_address": "string", // Primary wallet public key
"attestation_type": "enum", // "social" | "proof_of_humanity" | "domain"
"attestation_data": {
"platform": "string", // "twitter" | "github" | "domain"
"handle": "string", // @username or domain.com
"verification_signature": "string"
},
"validity_period": "number", // Seconds until revocation check
"revocation_list": "string" // IPFS CID for revocation registry
}Appendix B: Threat Model Matrix
| Threat | Attack Vector | Mitigation | Residual Risk |
|---|---|---|---|
| Content Impersonation | Register stolen content before original creator | Identity attestation, community reporting | Low - temporal precedence still verifiable |
| Hash Collision | Generate content with same SHA-256 hash | Cryptographic impossibility (2^256 space) | Negligible |
| Sybil Registration | Mass register content with fake identities | Rate limiting, identity verification, fees | Medium - economic deterrent |
| UI Spoofing | Fake attribution badges or registry data | Widget cryptographic verification | Low - verifiable through blockchain |
Appendix C: Glossary
Attribution Infrastructure: Systems that establish verifiable connections between creators and digital content without determining legal ownership.
Content Fingerprint: Cryptographic hash (SHA-256) that uniquely identifies digital content without revealing the original file.
Temporal Precedence: Immutable proof of registration order established through blockchain timestamps.
Competing Claims: Multiple registrations for identical content fingerprints, displayed chronologically.
Identity Attestation: Cryptographic binding between wallet addresses and external identity proofs (social media, domains, etc.).
Auxiliary Similarity: Community-driven or linking of visually similar content with different fingerprints.
Evidence Object: Structured data containing attribution facts (precedence, identity, claims) for policy engine consumption.
Registry Neutrality: Infrastructure that provides verifiable facts without making ownership or accuracy judgments.
Why Verifiable Attribution Infrastructure is Essential for Digital Media Ecosystems
As AI-generated content proliferates and global digital media consumption reaches unprecedented scale, the ability to make informed attribution decisions becomes foundational to maintaining trust, protecting creator livelihoods, and ensuring platform sustainability. Without verifiable attribution infrastructure, digital media ecosystems face inevitable degradation as information asymmetries compound and stakeholders lose confidence in content authenticity.
The Trust Imperative
Digital media platforms are fundamentally trust systems. When users cannot verify content attribution, they make suboptimal decisions about what to share, support, or believe. This erodes the foundation of creator economies, platform engagement, and democratic discourse.
Verifiable attribution infrastructure restores the information symmetry necessary for informed decision-making, enabling stakeholders to evaluate content based on evidence rather than assumption or platform-specific signals that may be manipulated or incomplete.
The Scale Requirement
Manual attribution verification cannot scale to billions of daily content decisions across global platforms. Only automated, cryptographically-backed systems can provide the speed, consistency, and reliability required for internet-scale attribution verification.
Trust Engine provides this infrastructure layer, enabling platforms to make attribution decisions based on immutable evidence while preserving creator privacy and maintaining cross-platform interoperability essential for modern multi-platform creator ecosystems.
Public, verifiable attribution infrastructure is not optional for the future of digital media—it is essential for preserving trust, protecting creators, and enabling informed participation in an increasingly complex and AI-augmented content ecosystem.
Conclusion
Trust Engine addresses the fundamental challenge of uninformed decision-making in digital media attribution by providing verifiable, tamper-evident evidence that stakeholders can reference instantly. By transforming attribution from subjective judgment into objective evidence evaluation, Trust Engine enables better decisions for consumers, creators, platforms, and legal systems at internet scale.
Through immutable temporal precedence, verified creator identities, transparent competing claims, and privacy-preserving architecture, Trust Engine provides the missing infrastructure layer that enables evidence-based attribution decisions at the scale and speed required by global digital media platforms. The result is a more trustworthy, transparent, and creator-friendly digital media ecosystem where informed decisions replace guesswork.